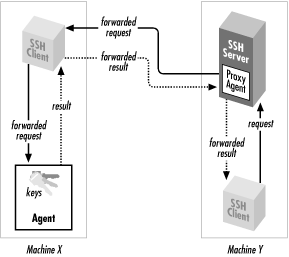
Ssh-agent.exe stores private keys used for public key authentication ssh-add.exe adds private keys to the list allowed by the server ssh-keyscan.exe aids in collecting the public SSH host keys from a number of hosts sftp.exe is the service that provides the Secure File Transfer Protocol, and runs over SSH. Secure Shell (SSH): SSH, also known as Secure Socket Shell, is a network protocol that provides administrators with a secure way to access a remote computer. SSH also refers to the suite of. Ssh.exe, which is the SSH client component that runs on the user's local system; ssh-keygen.exe generates, manages and converts authentication keys for SSH; ssh-agent.exe stores private keys used for public key authentication; ssh-add.exe adds private keys to the list allowed by the server. Mar 08, 2020 Appendix 1: Installing the Windows Terminal App. You can go directly to the Windows Terminal app store page by running the following command in PowerShell: As is well known, using Windows Terminal.
Server Setup – LDAP
NOTE: SWITCH OFF SELinux
# yum install migrationtools openldap-servers openldap openldap-clients openldap-devel
make entry in /etc/hosts
192.168.1.3 domain.com
Run this Command and copy output
# slappasswd
Note: Enter desired password here
pass:
confirm:
Output will like this, copy it
{SSHA}AuOU1S01Nj+gQ9FIHf8gCompENETugiT
Open the olcDatabase={1}bdb.ldif file and make the modifications shown
below to it.
# vi /etc/openldap/slapd.d/cn=config/olcDatabase={2}bdb.ldif
Next, add the following 3 lines to the end of the file (replace the SSHA
string with the string saved earlier)
allow users to modify their passwords, etc, you will have to add the
following after the last olcDbIndex line in this file, again replace the
domain name with yours.
Next modify the monitoring configuration file with our domain. Again,
change all references to my-domain with your domain.
# vi /etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif
Now it’s time to setup the LDAP database
# cd /usr/share/openldap-servers/
# cp DB_CONFIG.example /var/lib/ldap/DB_CONFIG
# chown -Rf ldap:ldap /var/lib/ldap
Setup a certificate for TLS, first edit /etc/sysconfig/ldap, uncomment
SLAPD_LDAPS and change from ‘no’ to ‘yes’.
# vi /etc/sysconfig/ldap

SLAPD_LDAPS=yes
# openssl req -new -x509 -nodes -out /etc/pki/tls/certs/slapdcert.pem
-keyout /etc/pki/tls/certs/slapdkey.pem -days 365
This will create the two required keys in the /etc/pki/tls/certs/ directory.
Now we need to make them readable:
# chown -Rf root:ldap /etc/pki/tls/certs/$cert.pem
# chmod -Rf 750 /etc/pki/tls/certs/$key.pem
Test the configuration, start the LDAP server and set it to start at boot.
# slaptest -u
config file testing succeeded
# service slapd start
# chkconfig slapd on
# vi /etc/openldap/ldap.conf
TLS_CACERT /etc/pki/tls/certs/slapdcert.pem
Below steps for easiness for creating ldif files
# vi /usr/share/migrationtools/migrate_common.ph
Without going to editing more, run this command
:%s/padl/ip-10-160-31-68/g
# vi /usr/share/migrationtools/migrate_passwd.pl
On line Number: 201 (after line shadowAccount)
Add this line also:
print $HANDLE “objectClass: ldapPublicKeyn”;
# ldapsearch -x -b “dc=domain,dc=com”
Create a file named /etc/openldap/init.ldif and below line
now you have to add that file in LDAP server
# ldapadd -x -D “cn=Manager,dc=domain,dc=com” -W -f /etc/openldap/init.ldif
It will now ask for password, paste or type the password that you typed for “slappasswd”
Now import any user from linux passwd file
# useradd manish
# passwd manish

# grep manish /etc/passwd > passwd.manish
# /usr/share/migrationtools/migrate_passwd.pl passwd.manish manish.ldif
# ldapadd -x -D “cn=Manager,dc=domain,dc=com” -W -f manish.ldif
It will ask for the rootdn passwd, provide that.
TEST LDAP SERVER: On LDAP Server
# ldapsearch -x -b “dc=domain,dc=com”
——————————————————————————————
LDAP Client Setup
# yum install nss-pam-ldapd openldap-clients
make entry in /etc/hosts
192.168.1.3 domain.com
now run this command: (This is to enable client authentication on SSH logins using LDAP server)
# authconfig –useshadow –usemd5 –enableldap –enableldapauth –ldapserver=domain.com –ldapbasedn=”dc=domain,dc=com” –enablemkhomedir –updateall
edit /etc/openldap/ldap.conf and add below lines
Now Test LDAP Client for auth:
1: ldapsearch -x
2: getent passwd | grep manish (though the user manish do not exists in client system, you shoukd get answer for this)
3: ssh -l manish 192.168.1.3
4: su – manish (though the user manish do not exists in client system, you should get login for this)

Now edit the slapd.conf
# vi /etc/openldap/slapd.d/cn=config/cn=schema/cn={21}openssh-lpk.ldif
Save and exit
Restart slapd.
# yum install httpd httpd-devel httpd-tools php php-common php-cli php-devel php-gd php-mbstring php-mcrypt php-mysql php-ldap phpldapadmin
Before login, edit file, /etc/phpldapadmin/config.php, go to line no. 398. Uncomment dn line and comment uid line, if it’s not already.
$servers->setValue(‘login’,’attr’,’dn’);
//$servers->setValue(‘login’,’attr’,’uid’);
Now log into phpLDAPadmin and browse to the user you want to attach an SSH key to:
user: cn=Manager,dc=website-domain,dc=com
pass: <LDAP Password>
——————————————————————————————
OpenSSH is the open-source version of the Secure Shell (SSH) tools used by administrators of Linux and other non-Windows for cross-platform management of remote systems.OpenSSH has been added to Windows as of autumn 2018, and is included in Windows 10 and Windows Server 2019.
SSH is based on a client-server architecture where the system the user is working on is the client and the remote system being managed is the server.OpenSSH includes a range of components and tools designed to provide a secure and straightforward approach to remote system administration, including:
- sshd.exe, which is the SSH server component that must be running on the system being managed remotely
- ssh.exe, which is the SSH client component that runs on the user's local system
- ssh-keygen.exe generates, manages and converts authentication keys for SSH
- ssh-agent.exe stores private keys used for public key authentication
- ssh-add.exe adds private keys to the list allowed by the server
- ssh-keyscan.exe aids in collecting the public SSH host keys from a number of hosts
- sftp.exe is the service that provides the Secure File Transfer Protocol, and runs over SSH
- scp.exe is a file copy utility that runs on SSH
Documentation in this section focuses on how OpenSSH is used on Windows, including installation, and Windows-specific configuration and use cases. Here are the topics:
Additional detailed documentation for common OpenSSH features is available online at OpenSSH.com.
Stores Shell
The master OpenSSH open source project is managed by developers at the OpenBSD Project.The Microsoft fork of this project is in GitHub.Feedback on Windows OpenSSH is welcomed and can be provided by creating GitHub issues in our OpenSSH GitHub repo.
